![]()
Why perform an IT Risk Rating?
Foremost, to demonstrate that due diligence has been applied before the decision to fund an initiative is made by investors, or before the decision to apply for funding is made by an organization seeking investment. An IT Risk Rating essentially provides the added confidence that the recipient of this funding has the capability to deliver. Financial control is not enough. Failures and cost overruns needlessly tarnish the reputation of both investing organizations and organizations that benefit from investments.
The most common consequences of ineffective or no risk management are the excessive time spent by managers in dealing with unanticipated difficulties and losses that prevent them from attending to other important issues, the deterioration in public image, the loss of customers, the reduction in forecasted growth and cash flow, and the abandonment of strategically desirable projects because of an inherent inability in managing loss exposures, not to mention the frustration of personnel who carry out their activities in an atmosphere of impending disaster.
What information does an IT Risk Rating provide?
An IT Risk Rating summarizes the global risk associated with an initiative using a financial-like rating. Among other things, it identifies and assesses risks to which the initiative is exposed, as a function of the envisioned or currently applied management and development approaches. In addition to the rating itself, the information provided includes corrective actions that should be implemented on a priority basis in order to achieve a conclusive delivery of the products or services targeted by the initiative.
The information provided as part of an IT Risk Rating is used to reduce both the frequency and significance of problems that result from risks that have materialized. Such an outcome will inherently increase the chances of delivering the products and services targeted by the initiative on schedule, within budget and with the required functionality.
How is an IT Risk Rating performed?
An IT Risk Rating is based on the concept of data fusion, which is defined as the use of techniques that combine data from multiple sources and gather that information in order to achieve inferences, which will be more efficient than if they were achieved by means of a single source.
Therefore, an IT Risk Rating combines the vast quantity of information acquired and processed by people as part of their regular activities, the bias removal and information processing algorithms of the PRC Samurai solution, and the analysis skills of the Risk Analyst.
Generating a meaningful IT Risk Rating, along with the information that supports this rating, can be a daunting task unless it is supported by appropriate methods and tools. Given the large number of interactions that lead to either success or failure, statements such as the one made by Napoleon Bonaparte, to the effect that all he wanted from his generals is that they be lucky, are therefore not entirely surprising.
PRC Samurai has specifically been designed to perform IT Risk Ratings.
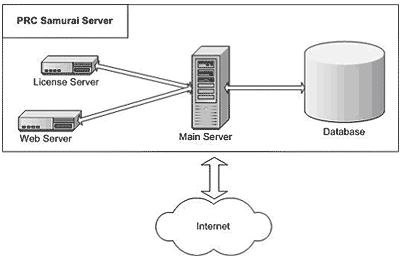
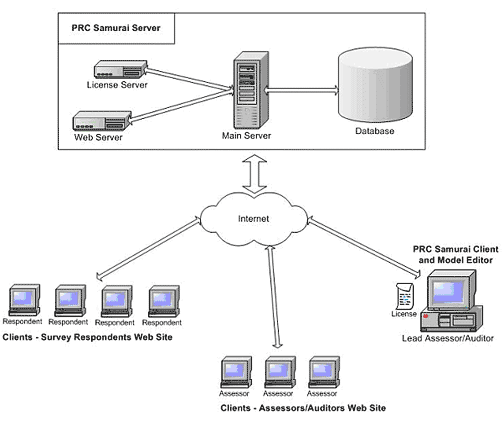
1. PRC Samurai Architecture
2. Software Components
There are three primary software components that make up the PRC Samurai System (see diagram above):
- PRC Samurai Server
- PRC Samurai Client / Model Editor
- Assessors / Respondents Web Sites (no installation required)
Component 2 needs to be installed on the Risk Analyst's computer. The
third component is the web site, which is accessible through any internet
browser.
The following sections further define product and platform specifications
required to properly install and use the PRC Samurai system.
2.1 PRC Samurai Server
This component is installed on GRafP Technologies' servers. The PRC Samurai Server includes several sub components such as the main server, license/authentication server, web application and Database.
This component processes and transmits data between the clients and the database and requires some platform software described in section 3.2.2 PRC Samurai Client and Model Editor
The PRC Samurai Client is installed in the Risk Analyst's computer that will be used to coordinate and lead best practices-, risk management-, and compliance-related activities (e.g. surveys, appraisals, assessments, audits, quality assurance, risk management, compliance, and governance). This computer must have access to Internet in order to send and receive data via the PRC Samurai Server.A model editor is also installed with the client, providing the Risk Analyst the flexibility to create or edit models characterized as either 'Public' or 'Private'.
2.3 Assessors / Respondents Web Clients
Two Web clients also make up the PRC Samurai System, one fulfilling the role of "respondent" for the conduct of survey-related activities to collect information, and another Web client fulfilling the role of "assessor" for the conduct of independent/verification-related activities in the customer's area of business. Both Web clients are accessible through the internet using any internet browser. Each participant logs into his or her respective Web site via a username and password provided by the Risk Analyst utilizing the PRC Samurai Client (section 2.2. above).
3. Component Specifications
3.1 PRC Samurai Server
3.1.1 Processor
The PRC Samurai Server has been tested using processor speeds of at least 1.5 GHZ.
3.1.2 Operating System
Linux (any distribution) or Windows (XP, NT, ME, 2000, Vista).
3.1.3 Memory
The PRC Samurai Server has been tested using processor memory size of at least 512MB.
3.1.4 Disk Storage
The PRC Samurai Server has been tested using disk storage capacity of at least 200 MB (10MB is needed for initial application and data management).
3.1.5 Platform Software
The platform software requirements for PRC Samurai are:
- JRE1.4.2, or later (required to execute the java code)
- Mysql 4.1, or later (required for the database management system)
- Apache 2.2 + Tomcat 5.0 (current web server and applications container)
3.1.6 Communication Protocol
The following communication protocols are required:
- TCP / IP
- HTTP
3.2 PRC Samurai Client and Model Editor
3.2.1 Processor
The computer in which the client is installed must have a processor speed of at least 1.5 GHZ. It also should allow for the proper execution of software packages described in section 3.2.5.
3.2.2 Operating System
The computer in which the client is installed must have a Windows (XP, NT, ME, 2000, Vista) operating system.
3.2.3 Memory
The computer in which the client is installed must have at least 512MB of internal memory.
3.2.4 Disk Storage
The computer in which the client is installed must have a minimum disk storage capacity of 100 MB.
3.2.5 Platform Software
The client software will generate reports that can be opened using:
- RTF Reader (like Microsoft Word)
- PDF Reader (like Acrobat reader)
3.2.6 Communication Protocol
The following communication protocols are required for the computer in which the client is installed:
- TCP / IP
3.3 Assessors / Respondents Web Clients
Users filling in the roles of "Assessors" and "Respondents" simply require a computer connected to internet and an internet browser in order to access their designated web sites.
The browser should be Internet Explorer 6.0 (or later) or Mozilla (1.0 or later), with Javascript enabled.